CUI vs FCI Under 48 CFR Final Rule: Defense Contractor Guide 2025
CUI vs FCI: What Defense Contractors Must Know Under the 48 CFR Final Rule
Key Takeaways
Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) differ fundamentally in sensitivity and legal requirements, impacting cybersecurity controls and contract eligibility.
The 48 CFR Final Rule clarifies classification boundaries, documentation expectations, and flow-down obligations to subcontractors.
Accurate classification aligned with CMMC certification levels is critical to avoid compliance failures and avoidable costs.
Introduction: The Final Rule Has Redrawn the Lines
TL;DR: The recently finalized 48 Code of Federal Regulations (CFR) rule settles long-standing confusion between CUI and FCI. For defense contractors, especially those navigating CMMC 2.0 requirements, distinguishing these categories is not just academic, it dictates how you plan and prove your cybersecurity defenses.
Understanding whether your data qualifies as CUI or FCI shapes your System Security Plan (SSP), controls implementation, audit readiness, and ultimately your contract eligibility. Misclassification risks compliance violations and lost business opportunities.
This guide provides a definitive and updated overview grounded in the 48 CFR Final Rule, NARA’s CUI Registry, DFARS clauses, and the CMMC framework, empowering contractors of all sizes to confidently manage and document data classification.
Updated Definitions and Regulatory Context
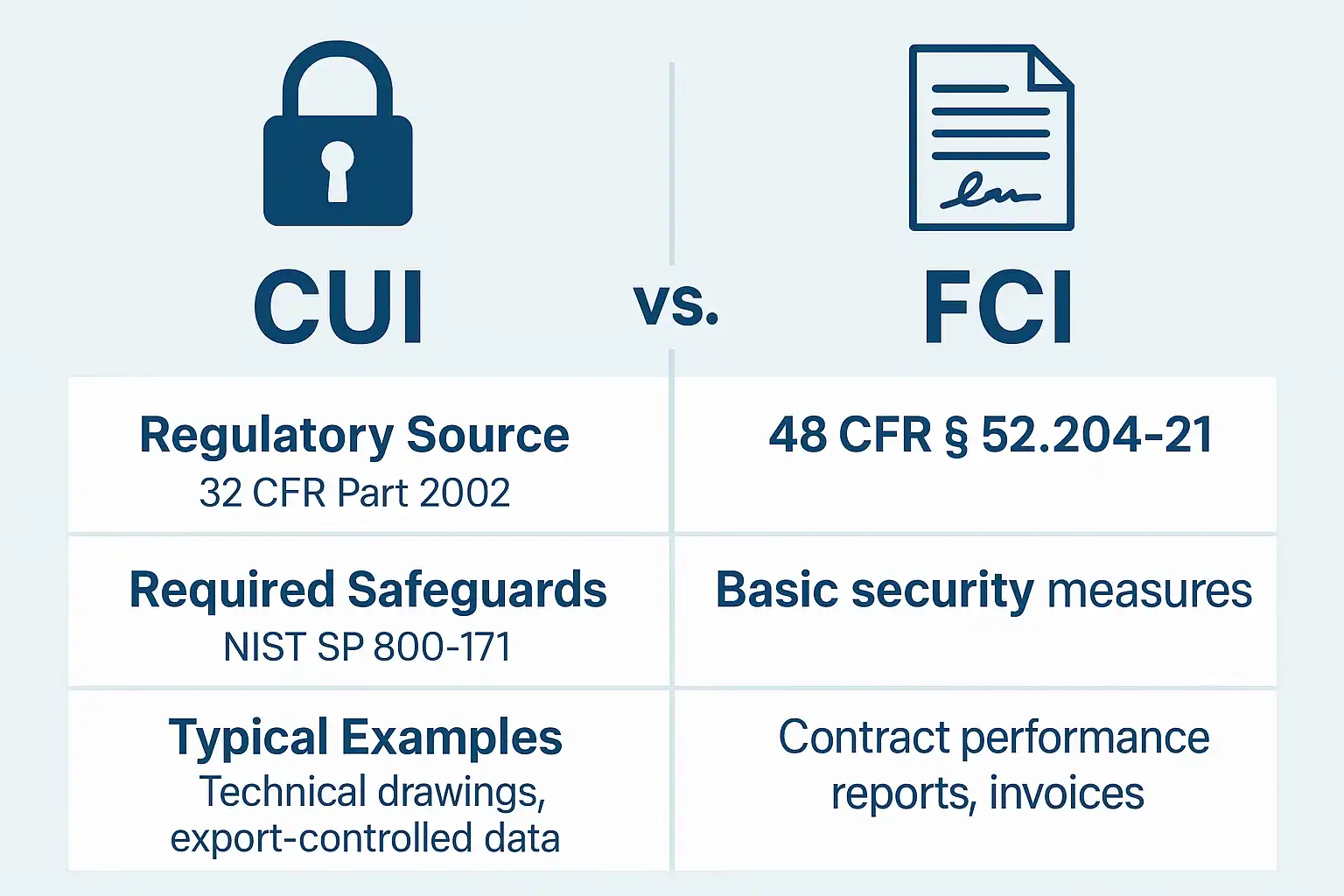
| Category | Controlled Unclassified Information (CUI) | Federal Contract Information (FCI) |
|---|---|---|
| Category: Governing Source | Controlled Unclassified Information (CUI): 32 CFR Part 2002; NARA CUI Registry | Federal Contract Information (FCI): 48 CFR 2.101 (definition); FAR 52.204-21 (safeguarding requirements) |
| Category: What It Is | Controlled Unclassified Information (CUI): Government-created or possessed information requiring safeguarding per laws/regulations. | Federal Contract Information (FCI): Nonpublic contract-related data provided by or generated for Government under a contract. |
| Category: Required Safeguards | Controlled Unclassified Information (CUI): NIST SP 800-171 (CUI Basic) or higher | Federal Contract Information (FCI): FAR 52.204-21 (minimum CMMC Level 1) |
| Category: Common Examples | Controlled Unclassified Information (CUI): Technical drawings, system vulnerability reports, export-controlled data | Federal Contract Information (FCI): Project schedules, internal pricing, unmarked DoD correspondence |
| Category: CMMC Applicability | Controlled Unclassified Information (CUI): Level 2 (Protect CUI + FCI) | Federal Contract Information (FCI): Level 1 (Protect FCI only) |
Bottom line: FCI is contract-centric information protected primarily from public disclosure, whereas CUI represents sensitive but unclassified information requiring legal safeguarding controls.
How CMMC Certification Levels Align With CUI and FCI
The Cybersecurity Maturity Model Certification (CMMC) program ties data classification directly to required cybersecurity controls:
Level 1 (Foundational): Protects FCI exclusively, applying 17 controls from FAR 52.204-21.
Level 2 (Advanced): Applies to environments handling CUI and any associated FCI, requiring all 110 controls in NIST SP 800-171 Rev 2.
Level 3 (Expert): Intended for specialized programs, adding NIST SP 800-172 controls.
Mislabeling data may lead to either insufficient protection (if CUI is mistaken for FCI) or unnecessary expenditure (if all data is treated as CUI). Correct classification ensures compliance scope matches actual risk and contract requirements.
What the 48 CFR Final Rule Clarifies
Explicit Boundary: FCI is strictly defined as contract-generated or provided data; CUI includes data protected under laws such as ITAR, Export Control, and Privacy Act authorities.
Documentation: Contractors must record their classification rationale within the SSP or related artifacts. For audit readiness, incorporating detailed evidence and logs is critical, aligned with CMMC Level 2 assessment evidence expectations.
Assessment Expectations: CMMC assessors require traceability linking contract clauses, data categories, and classification labels.
Flow-Down Rules: Subcontractors handling CUI must fully implement NIST 800-171. Those dealing only with FCI follow FAR 52.204-21. For granular guidance on subcontractor protections, see anonymizing CUI subcontractors.
Consistent Categories: NARA’s Registry updated to reflect DoD’s critical infrastructure, export control, defense technical data, and others.
"Classification is no longer a theoretical exercise but a traceable, auditable enterprise woven into compliance documentation."
Real-World Examples of Classification
CUI Includes:
System penetration test results or vulnerability scans on DoD systems.
Technical drawings and CAD files based on government-furnished information.
System architecture documents or interface specifications.
Export-controlled info governed by ITAR or EAR regulations.
FCI Includes:
Contract schedules and project management data not publicly releaseable.
Timekeeping, labor cost reports for billing purposes.
Confidential pricing and proposal documents submitted to the DoD.
Internal communications connected to contract performance, but not marked CUI.
Edge Cases
| Scenario | Classification | Explanation |
|---|---|---|
| Scenario: Internal, public-source data about DoD agency | Classification: Not CUI | Explanation: Public source data, no safeguarding legally required. |
| Scenario: ERP reports summarizing DoD deliverables | Classification: FCI | Explanation: Contract-generated data, non-public. |
| Scenario: Contractor penetration test report for DoD system | Classification: CUI | Explanation: Reveals controlled vulnerability information. |
Mapping Classification to CMMC Domains
| CMMC Domain | Control Focus | CUI/FCI Impact |
|---|---|---|
| CMMC Domain: Access Control (AC) | Control Focus: Limit access to authorized personnel | CUI/FCI Impact: CUI requires strict role-based controls; FCI demands basic access restrictions. |
| CMMC Domain: System & Communications Protection (SC) | Control Focus: Encryption in-transit and at-rest | CUI/FCI Impact: Mandatory for CUI; recommended for FCI. |
| CMMC Domain: Risk Management (RM) | Control Focus: Identify and mitigate risks | CUI/FCI Impact: Maintain accurate, up-to-date data classification inventories. |
| CMMC Domain: Audit & Accountability (AU) | Control Focus: Log and monitor system activity | CUI/FCI Impact: Essential to log CUI access; helpful for FCI oversight. |
| CMMC Domain: Configuration Management (CM) | Control Focus: Manage and track system changes | CUI/FCI Impact: Critical for CUI environments to preserve integrity. |
Practical Steps for Contractors
Identify and Categorize Data Early Review contract clauses, especially DFARS 252.204-7012, 7019, 7020, for CUI applicability. Maintain a data inventory detailing sources and classification.
Label and Store Correctly - Label CUI clearly, e.g.,
CUI//DEFENSE//EXPORT. Store it in secured environments compliant with NIST SP 800-171 standards. - Mark FCI as "For Official Use Only" or a similar designation within systems compliant with FAR 52.204-21.Manage Mixed Data Environments Carefully When CUI and FCI coexist, apply CUI-level controls to the entire system unless isolated via logical segmentation.
Document Your Classification Rationale Within your SSP, cite contract clauses, specify data categories, and explain classification decisions to facilitate assessor verification. Ensure inclusion of detailed evidence and documentation per CMMC Level 2 evidence requirements.
Review Classification Regularly Update classifications when contracts change, new government data is received, or system boundaries shift.
Common Misclassification Pitfalls
Treating all contract information as CUI without legal basis.
Overlooking derived data generated from CUI sources, these must remain protected as CUI.
Neglecting to update SSPs and classification data after any reclassification event.
Assuming FCI is not subject to controls; it still demands foundational safeguards per FAR 52.204-21.
Conclusion: Classification Underpins Compliance Success
Misclassification stands as a leading cause of failed CMMC assessments. The 48 CFR Final Rule demands not only safeguarding the correct data but also proving classification accuracy with robust documentation.
A disciplined, transparent classification program, consistent with NARA, DFARS, and NIST guidance, forms your strongest shield against compliance risks and fosters trust with Department of Defense partners.
"Pro Tip: Leverage a dedicated CUI/FCI classification checklist or a cloud-based compliance platform to centralize labeling, evidence collection, and documentation. This approach transforms classification from a chore into a streamlined, scalable process."
Frequently Asked Questions
Is vulnerability data CUI?
Yes. Vulnerability data tied to DoD systems, including scans and penetration tests, is considered CUI due to its sensitive nature.
Does timekeeping data qualify as FCI?
Yes. Contract labor and time reports are FCI; they must be protected from public disclosure under contractual terms.
Is data created about a DoD agency from public sources classified as CUI?
No. Data compiled solely from public information does not constitute CUI.
Can FCI become CUI?
Yes. If FCI incorporates or derives from CUI (such as summaries containing controlled technical data), it assumes CUI classification.
Do subcontractors have identical protection requirements for FCI and CUI?
No. Subcontractors protecting FCI must comply with FAR 52.204-21, corresponding to CMMC Level 1, while those handling CUI must meet full NIST 800-171 requirements for Level 2.
What distinguishes CUI Basic from CUI Specified?
- CUI Basic: Requires NIST SP 800-171 safeguards and general handling rules. - CUI Specified: Subject to additional dissemination and marking rules dictated by specific laws or regulations like ITAR or the Privacy Act.
What's the best way to document classification for assessments?
Include detailed data types, associated contract clauses, and classification rationale within your System Security Plan or data inventory to make your process transparent for assessors.
Understanding and applying these distinctions guided by the Final Rule allows contractors to sharpen their cybersecurity posture, simplify compliance, and strengthen government partnerships. Sound data classification is not just compliance, it's a competitive advantage.
Ready to simplify your CMMC compliance and classification process?
Sign up for the CMMC Dashboard to access tools that streamline your evidence collection, documentation, and assessment readiness.
Sources: 48 CFR Final Rule (effective 2025), NARA CUI Registry, DFARS 252.204-7012, FAR 52.204-21, NIST SP 800-171 Rev 2, CMMC Model Version 2.0.